[ad_1]
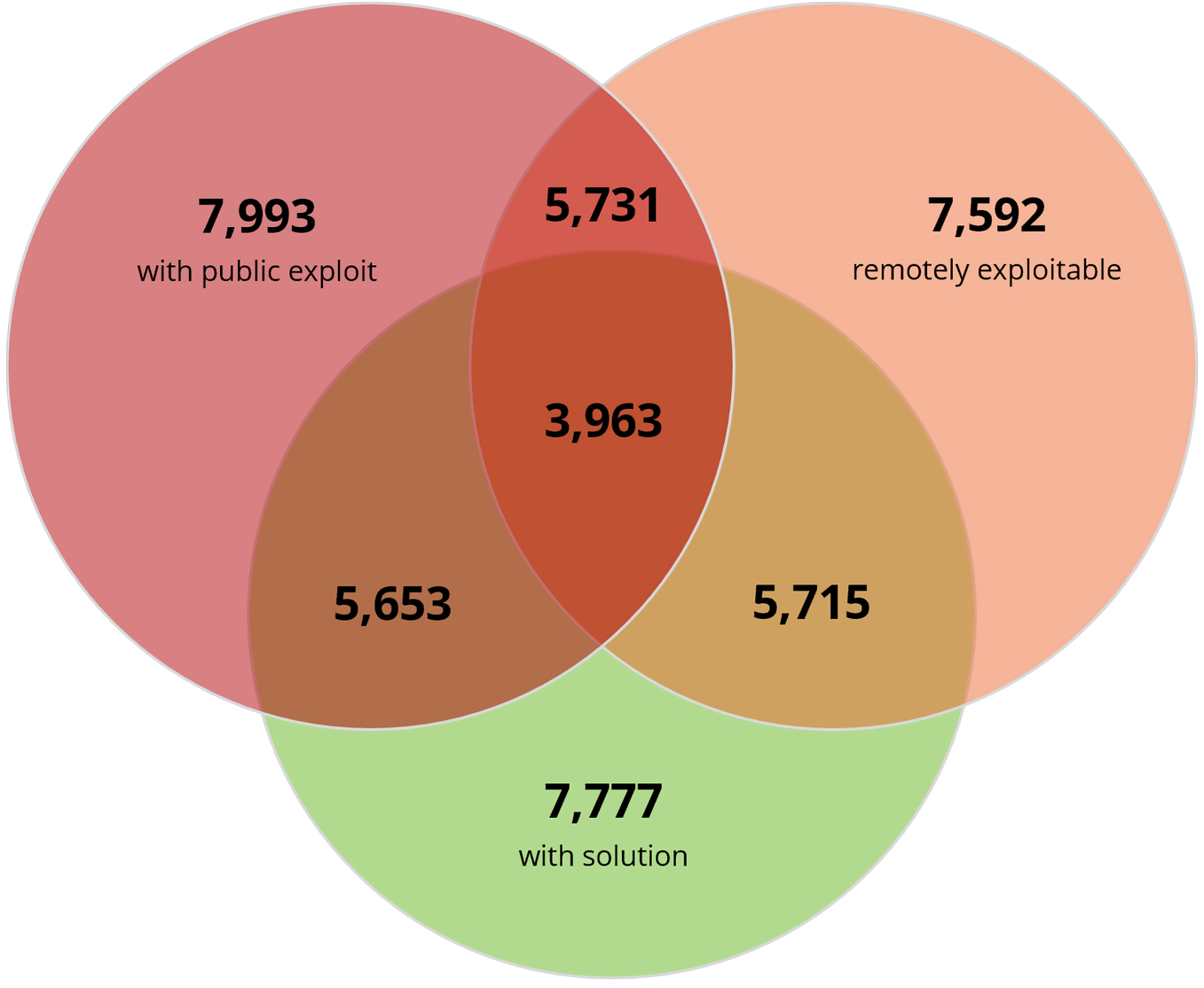
What just happened? Third-party WordPress plugin vulnerabilities increased significantly in 2021, and many of them still have known public exploits. Cybersecurity firm Risk Based Security said 10,359 vulnerabilities were reported to affect third-party WordPress plugins at the end of last year, of which 2,240 were disclosed in 2021. That’s a 142 percent increase compared to 2020, but the bigger concern is the fact that 77 percent of all known WordPress plugin vulnerabilities – or 7,993 of them – have known public exploits.
A closer look revealed that 7,592 WordPress plugin vulnerabilities are remotely exploitable while 4,797 have a public exploit but no CVE ID. For organizations that only rely on CVEs for mitigation prioritization, the latter means that more than 60 percent of vulnerabilities with a public exploit won’t even be on their radar.
Another issue Risk Based Security touched on for organizations is their focus on criticality rather than exploitability.
The firm notes many organizations categorize vulnerabilities with a CVSS severity score below 7.0 as not being high priority, and thus don’t address them right away. That’s a problem considering the average CVSS score for all WordPress plugin vulnerabilities is 5.5.
Risk Based Security and others have observed malicious actors favoring vulnerabilities not with high severity scores, but rather those that can be easily exploited. Given the data and observations, perhaps it would be wise for some organizations to reconsider their threat management protocols.
Image credit: Justin Morgan
[ad_2]
Source link















